Key Management Strategy and Distribution of Public Key for Cloud Security
DOI:
https://doi.org/10.31033/ijemr.13.1.17Keywords:
Hypertext Transfer, Public Key, Transport Layer, Honeycomb Technique, CryptographyAbstract
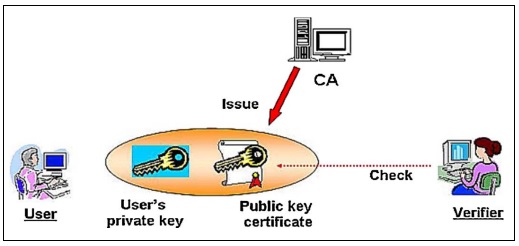
The security perspective of cloud systems has developed Hypertext transfer protocol secure (HTTPS), Use case of determination of the public key is widely used in Transport Layer Security for the system. Three components, including storage servers, data storage, and blocking stockpiling, were used to categorise online storage. The limitation is that the waiting period falls inside the time window j > j in order to guarantee advance assurance. The constants for the honeycomb techniques must fulfil the condition that m 2ndlog QE in order to ensure the integrity of the q-module arithmetic lattices. Asymmetrical data cryptography and bilateral cryptography are indeed the two types of key decryption techniques used in authenticating methods. The main goal of encryption is to create secure data for communication links.
Downloads
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Kiran Jain

This work is licensed under a Creative Commons Attribution 4.0 International License.











