Securing the Cloud: An Empirical Study on Best Practices for Ensuring Data Privacy and Protection
DOI:
https://doi.org/10.31033/ijemr.13.2.6Keywords:
Cloud Computing, Cloud Security, Cyber Threats, Insider Attacks, Cloud ArchitectureAbstract
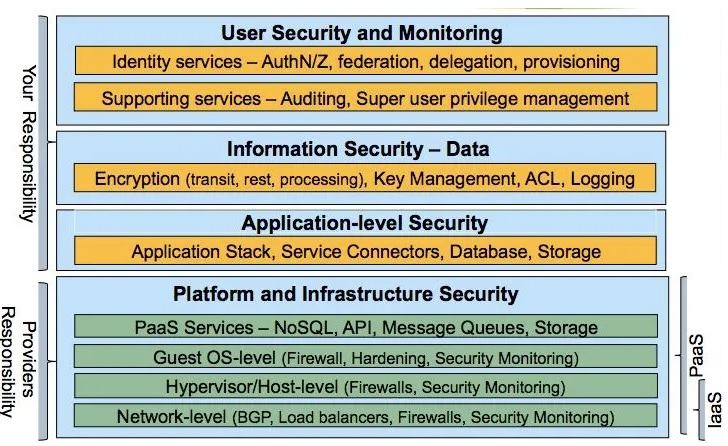
Cloud computing has emerged as a powerful paradigm that provides on-demand access to shared computing resources, such as computing power, storage, and applications, over the internet. It offers unparalleled scalability, flexibility, and cost-efficiency, making it increasingly popular among businesses and individuals alike. However, with the increasing reliance on cloud computing, security concerns have also become a critical issue that needs to be addressed to ensure the confidentiality, integrity, and availability of data and services in the cloud. Cloud security refers to the set of measures and practices designed to protect cloud-based resources and data from unauthorized access, data breaches, data loss, and other security threats. It encompasses a wide range of security challenges, including data privacy, access control, data integrity, compliance, legal issues, identity and access management, and risk assessment. Addressing these challenges is crucial to ensure the trustworthiness and reliability of cloud computing environments. The importance of cloud security cannot be overstated. Organizations need to have robust security measures in place to protect their sensitive data and critical applications from potential cyber threats, insider attacks, and other security risks. Cloud service providers also need to implement stringent security mechanisms to safeguard their customers' data and ensure compliance with relevant regulations and standards. To effectively address cloud security challenges, extensive research and development efforts have been undertaken in the field of cloud security. Literature on cloud security provides valuable insights into the state-of-the-art security mechanisms, best practices, and emerging trends in cloud security. This paper aims to provide an overview of the existing research and developments in cloud security, covering various aspects such as data privacy, access control, encryption, risk assessment, identity and access management, and more. In this paper, we delve into introduction to cloud ,advancements in cloud security and various reviews related to cloud architecture.
Downloads
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 N. Saranya, M.Sakthivadivel, G.Karthikeyan, R.Rajkumar

This work is licensed under a Creative Commons Attribution 4.0 International License.











