A Review Article on Authentication Protocols in Cloud Computing
DOI:
https://doi.org/10.31033/ijemr.13.2.38Keywords:
Cloud Computing, Security Issues, Authentication, AuthorizationAbstract
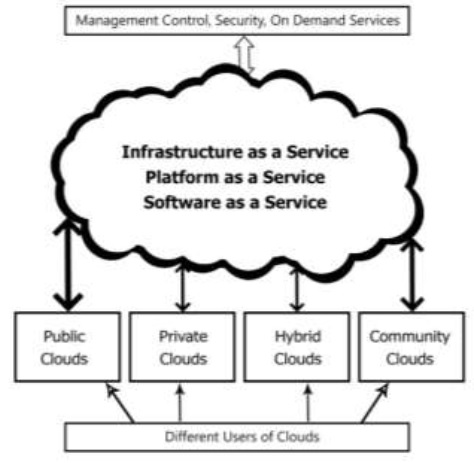
Cloud computing technology provides on demand computing resources like software, hardware and storage in pay-per-use model. Cloud computing is very beneficial for today’s organizations, as there is no need to maintain physical infrastructure. These services and resources can be accessed from anywhere anytime over the internet. It is cost effective as users only need to pay for resources they use. Many individuals and organizations have shifted themselves over cloud environment as it is cheaper and convenient. As huge amount of sensitive data is being stored and processing in cloud computing environment so there is major concern of security. Lack of security may cause several issues. It may result in loss of organisation’s data and may even leak confidential data of user and organisation to unwanted access. To implement security in cloud computing various authentication and encryption protocol exists. This aim of this paper is to review various authentication protocols given by various researchers all over the world.
Downloads
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2023 Umaima Fatima, Dr. Sheeba Parveen

This work is licensed under a Creative Commons Attribution 4.0 International License.











